Cybersecurity Technologies Part 2
November 3, 2025

Essential Software for Cybersecurity
Last week in Part 1 of our two-part series, we focused on the hardware and network technologies that protect your Ace Hardware store from cyberattacks. In this final article for Cybersecurity Awareness Month we’ll turn our attention to essential cybersecurity software — the tools that form your digital front line.
Remember: PCI compliance requires that safeguards not only be in place, but that your business can prove they are active, verifiable, and maintained.
Anti-Virus Software: The Foundation of Endpoint Protection
Every device that connects to your store network—computers, tablets, phones, and Zebras—needs protection from malicious software, or malware. Anti-virus (A/V) software detects and blocks threats like ransomware, spyware, and adware before they cause damage.
There are two main types of A/V protection:
- Passive A/V: Runs locally and relies on automatic updates to block known threats.
- Active A/V: Adds centralized monitoring, intelligent alerts, and real-time management by cybersecurity professionals.
Key features to look for:
- Centralized dashboard monitored by cybersecurity experts
- Lightweight software that won’t slow devices down
- Intrusion Prevention System (IPS) to block suspicious behavior—not just known threats
- Sandboxing to analyze and contain new, “zero-day” threats safely
- Automatic quarantining and cleaning of infected files
- Anti-theft protection for mobile devices
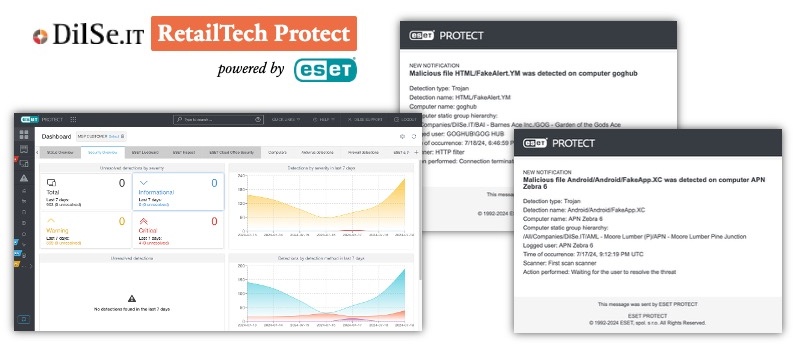
Important: Every store device must have managed anti-virus protection. A single unprotected laptop or Zebra device can compromise your entire network.
Business Email: Your Gateway and Guardrail
PCI rules require the use of a business-class email system — not personal accounts like Gmail, Yahoo, or Hotmail. Business email systems (for example, DilSe.IT RetailTech Business Email, Microsoft 365, or Google Workspace Business) provide enterprise-grade filtering, authentication, and control over who can send from your company’s domain.

How to tell you’re using business email: Your address ends with your store domain — like @mainstreetace.com — not a free public domain.
Business email is like living in a gated community: armed guards, cameras, and secure access rules keep intruders out. Personal email, by comparison, is like living on an open city street — you can hope the local police are on patrol, but you may still be vulnerable.
Business email security features include:
- Spam, phishing, and malware filtering before messages reach your inbox
- Authentication protocols (SPF, DKIM, DMARC) to ensure emails are legitimate
- Configurable rules for attachments, links, and sender restrictions
- Encryption to protect sensitive messages
Using personal email on store-owned computers is not PCI compliant and creates unacceptable risk.
Cloud-Based File Sharing: Safer, Smarter Storage
Business data stored only on a local hard drive is one ransomware attack — or one hardware failure — away from being lost forever. Modern cloud-based file storage solutions like DilSe.IT RetailTech File Share or Microsoft OneDrive, when implemented properly, securely back up and synchronize your documents in real time.

Advantages of cloud file storage:
- Access is controlled at user, group, and folder levels
- Automatic versioning and backups
- File sharing with secure links and expiration options
- Access from any device — desktop, mobile, or web
- Built-in ransomware recovery and rapid restore options
Best practice: Store 100% of your business files in a secure, cloud-based system. Never save critical files only to a local computer.
Password Vaults: Solving the Password Problem
Most employees juggle 50 to 100+ passwords across work and personal accounts. That’s more than anyone can safely remember—so people write them on sticky notes, reuse them, or choose simple, guessable passwords.

A password vault eliminates these risks by securely storing and managing credentials for each account. Modern business-grade password managers, such as DilSe.IT RetailTech Password Vault or 1Password, are essential tools for every Ace store.
What to look for in a password vault:
- Works across desktop, mobile, and browser
- Supports biometrics (Face ID, fingerprint)
- Stores both personal and shared logins securely
- Allows granular access by role, department, or user
- Automatically creates complex, unique passwords
- Integrates with multi-factor authentication (MFA)
- Uses strong, end-to-end encryption
Your store is only as secure as its weakest password — or the sticky note someone leaves behind.
The Bottom Line
Four types of software form the backbone of your store’s cybersecurity strategy:
- Anti-virus protection for all devices
- Business email for professional communication and filtering
- Cloud-based file sharing for secure, backed-up storage
- Password vault for managing strong, unique passwords
Cybersecurity requires both hardware and software working in harmony.
If you missed Part 1 of this series — on network and hardware security — be sure to check it out here.
We hope you have found our Cybersecurity Awareness Month articles over the past 5 weeks valuable. Thanks for reading and becoming cyber-aware… cybersecurity is a 24/7 x 365 task!