Cybersecurity Technologies Part 1
October 28, 2025

Network and Endpoint Protection
In last week’s article for Cybersecurity Awareness Month we discussed how employee training can prevent the 80 – 90% of breaches caused by human error. But even the best-trained team can’t defend an unprotected network. This week, in Part 1 of our two-part series, we’ll explore the technologies that form the backbone of your business’ cybersecurity. PCI compliance requires that specific safeguards be in place to protect your business from cyberattacks — and to prove that protection can be verified and sustained.
The Typical Small Business Network
Most small businesses operate with only partial protection. Anti-virus software is installed on workstations running accounting or ERP software, but other computers and mobile devices often remain unprotected and unmanaged. The network typically includes an unmanaged firewall, while the remaining switches, access points, and devices form what we call a “dumb network.”
These setups may appear to work, but they’re inherently fragile, insecure, and difficult to manage:
- No continuous monitoring or alerting
- Unknown or unauthorized devices can join the network
- Threats like malware or rogue equipment going unnoticed until it’s too late
- Inconsistent passwords and configurations across devices
- Missed firmware updates and security patches
- Employees or vendors connecting personal or consumer-grade devices
- Outages or breaches that take hours to diagnose because no log data exists
Computers not running accounting or ERP software, along with mobile devices and peripherals, may lack any protection or remote management. With no centralized oversight, the firewall becomes the only line of defense — leaving multiple openings for cyberthreats to exploit.

DilSe.IT Tech Protect: An Integrated Defense
Robust protection requires a comprehensive approach that combines endpoint security with an intelligently managed network. Every device — from accounting and ERP workstations to laptops, in-office servers, dedicated equipment workstations, and mobile devices — should be protected and remotely managed to ensure software, firmware, and operating systems remain up to date.
A fully monitored and managed network transforms your technology from a collection of independent devices into a unified, adaptive defense system built on three pillars: visibility, control, and response.
Visibility
- Every device is visible through a central controller.
- Traffic patterns are logged and analyzed — abnormal behavior (like a ERP terminal connecting to a foreign IP) triggers immediate alerts.
- Real-time dashboards, health monitoring, reports, and alerts become the “eyes and ears” of your cybersecurity posture.
Control
- Configurations are centrally enforced and cannot be changed without authorization.
- Automatic firmware patching closes vulnerabilities as they’re discovered.
- Network segmentation isolates systems like ERP, cameras, phones, office PCs, and guest Wi-Fi — preventing an infection in one area from spreading.
- Multi-factor authentication and role-based permissions ensure only authorized administrators can make changes.
Response
- Monitoring systems detect and alert your IT partner within seconds.
- Automated remediation can isolate a compromised device before it spreads malware.
- Historical logs enable forensic analysis — knowing when, how, and whysomething happened.
- Continuous uptime monitoring supports proactive maintenance instead of emergency firefighting.

It’s Not Just About the Hardware
Many small businesses use the UniFi (Ubiquiti) equipment recommended by DilSe.IT, but hardware alone doesn’t create cybersecurity. The true protection comes from how the network is designed, deployed, and managed.
- Without a central controller, each device runs in isolation, eliminating visibility and consistency.
- Without VLANs and segmentation, all traffic mixes together—allowing infections to move from a customer’s phone to a POS terminal.
- Without cloud management, firmware updates and threat intelligence are missed, leaving exploitable vulnerabilities.
- Without professional configuration, advanced protections like IDS/IPS, geo-blocking, and DNS filtering remain disabled.
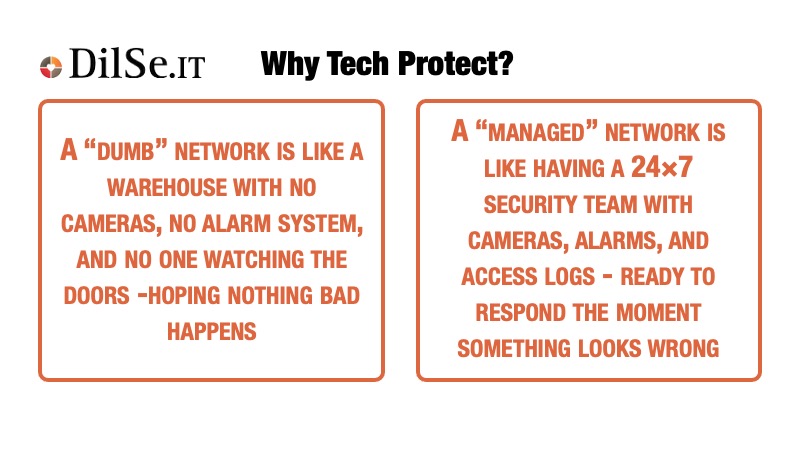
In simple terms…
A “dumb” network just passes traffic.
A “managed” network understands it, monitors it, controls it, and protects it.
The Bottom Line
Cybersecurity isn’t about the brand of equipment on the rack—it’s about intelligence, consistency, and control. A fully monitored and managed network protects your customer data, keeps your operations running, and gives you peace of mind knowing someone is watching your digital front door—even when you’re not.
Next week in Part 2 of this series, we’ll cover the software technologies that complete your cybersecurity foundation.