Are You Vulnerable to a Cyber Attack?
June 4, 2024
Many Ace Hardware retailers don’t see themselves as potential victims of a cyber attack. They believe they are too small to be noticed by cyber criminals who prefer to go after the big name retailers like Target or Home Depot. By the statistics, this is simply not true.
- More than 700,000 cyber attacks target small businesses each year
- Small businesses are 3 times more likely to be targeted by cyber criminals than larger companies
- An employee of a small business will experience 350% more social engineering attacks than an employee of a larger enterprise
Why is this true? Cyber criminals know that small businesses often lack the IT expertise and procedural controls that exist in larger businesses. In short, small businesses are easier targets with a higher likelihood of success for the cyber criminal.
Unfortunately, the consequences of a cyber attack for a small business can be severe.
- The average cost of a cyber attack on a small business is $30,000
- 60% of small businesses that suffer a cyber attack go out of business within 6 months
It is important for you to be aware of how a cyber criminal can attack your Ace retail store.
Cyber attack vectors for an Ace store
An attack vector is a way for a bad actor to enter your store’s systems or network. There are multiple vectors by which cyber criminals may try to attack an Ace Hardware store.
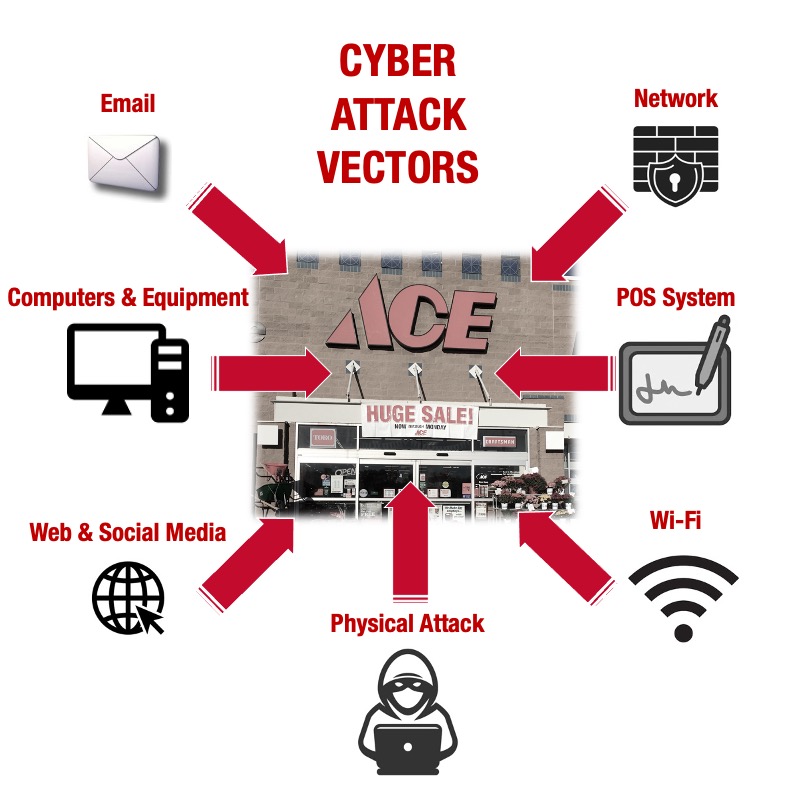
The physical attack vector
A physical attack involves the cyber criminal actually entering your store or remotely interacting with your employees. If the criminal enters the store they may attempt to physically access your computers to install malicious software – commonly called malware. Or, they may attempt to install a keyboard logger device between the keyboard cable and the USB port on the computer. Keyboard loggers capture every keystroke including login credentials and can transmit this data to the cyber criminal via Bluetooth or wi-fi. The criminal may attempt to install a card skimmer which captures cardholder data directly from the card itself as it is inserted or swiped on the signature capture pad.
With a social engineering attack, the criminal may try to trick your employees to giving them login credentials, allowing access to your systems, or transferring money. Social engineering attacks can occur in-person but they are much more likely to be accomplished over the phone, via email, or text message exchange.
The computers and equipment attack vector
Computers and equipment in your store and connected to your network offer multiple attack vectors for cyber criminals. Out-of-date computer operating systems and missing security patches provide loopholes for criminals to exploit to gain access to your systems. Microsoft is still supporting the Windows 10 operating system through October 2025. Earlier versions of Windows are no longer supported and represent a significant security risk to your business. It is also important that you regularly install operating system patches and updates as they become available. The preferred method is to do this manually on at least a monthly basis. Alternatively, you can turn-on automatic patches and updates. The risk of automatic updates is that occasionally these can cause systems such as Eagle point-of-sale to stop functioning correctly.
Computers without locking screen savers and strong passwords also create a vulnerability to attack. Criminals can easily gain access to these systems to install malware that can spread to affect other computers and your network.
We frequently find computers in an Ace store that are not behind a hardware firewall and that are not protected by antivirus software. Epicor requires that all computers running Eagle operate behind the Sonicwall firewall appliance. But, what about other computers in your store such as paint computers and training computers? These are not necessarily protected. Similarly, Epicor asks you to install the CaptureClient antivirus software on all of your Eagle computers. However, Epicor does not actively monitor CaptureClient and they do not know if you have replaced a computer and failed to install the antivirus software. Epicor does not worry about any non-Eagle computer such as the paint auto-tinter computer where we frequently find no antivirus software is running. Any inadequately protected computer connected to your network presents an attack vector.
Isolated copies of files stored on the hard drive of any computer are also a risk. If these files are not backed-up regularly, or better yet, replicated in a cloud-based file share they are vulnerable to malicious deletion or encryption through a ransomware attack.
The email attack vector
Business email compromise (BEC) was the second worst type of cyber crime in-terms of lost dollars in 2023 according to the US Secret Service. Many Ace stores use free personal email accounts for business purposes, for example Gmail, Hotmail, Yahoo, MSN, or AOL accounts. Free email accounts offer minimal protection against professional cyber criminals. Phishing for confidential information which can be used to exploit your business and spoofing to fool email users into revealing confidential information, clicking malicious links, or taking inappropriate, dangerous action are the most common and effective tactics used by cyber criminals.
Email attacks are used with social engineering to do direct, financial damage to your business – for example trying to trick a user into paying a fraudulent invoice. And, email attacks are used to install malware to extort more money through ransomware, or to steal information such as customer credit card data or confidential employee records.
The Web and social media attack vector
Most Ace Hardware stores only sell on-line through Acehardware.com where security responsibility falls on Ace Corporate. This typically makes a Web-based cyber attack a lesser concern for most Ace store owners. However, it is still possible for cyber criminals to inflict damage on your company’s reputation and brand through the Web or social media attack vector. For example, if a cyber criminal gets control of your Web domain they may demand a ransom to regain access to your Website or email. Likewise, a criminal gains access to your social media accounts they can cause you to lose access to hard-won followers either temporarily or permanently.
The network attack vector
Direct attacks on your company’s network can take a variety of forms. Denial of Service (DoS) attacks flood your network with excessive traffic causing legitimate traffic, such as credit card authorizations, to be blocked. Man-in-the-Middle (MitM) attacks intercept and may alter network communications between parties to steal data or inject malicious content. Brute force attacks are often used in-combination with credential stuffing using automated tools (bots) to try to guess login credentials by trying numerous combinations. Systems with out-of-date firmware, weak passwords, or the lack of an account lockout feature are especially vulnerable to these attacks.
The point-of-sale system attack vector
Attacks which target your point-of-sale system have the potential to be the most costly for your business. Loss of credit cardholder data can result in significant business interruption lasting days or weeks, severe reputational damage, and potentially hundreds of thousands of dollars in fines from credit card companies. Many Ace Hardware stores are not compliant with the Payment Card Industry Data Security Standard (PCI DSS) which increases your risk and exposure to financial harm. Weak passwords, incorrect security option settings, and lack of policies and procedures also contribute to the ease with which a cyber criminal can attack your point-of-sale system.
The wi-fi network attack vector
Wireless networks (wi-fi) can be an attractive attack vectors for cyber criminals. Many Ace stores don’t have their wi-fi network segmented to separate the cardholder data environment (CDE) from other company devices and/or personal devices. This can expose sensitive cardholder data to criminals. Employees can also unwittingly give a criminal access when they connect their infected personal device to the company network. Attackers search for vulnerable wireless networks and exploit weaknesses to gain unauthorized access and wreak havoc.
Potential cost of a cyber attack
The potential cost of a cyber attack can range from hundreds of thousands of dollars in the event of a cardholder data breach to a few hours of lost productivity in the event of a minor malware attack.

As stated at the beginning of this article, the average cost of a cyber attack on a small business is $30,000. When you compare that to your average shoplifting incident, the importance of closing the cyber attack vectors into your Ace Hardware store becomes clear.
To learn more about protecting your Ace store from cyber attacks, please contact us.